Hey there, tech enthusiasts and cloud wizards! If you're reading this, chances are you're diving headfirst into the world of IoT, SSH, and AWS. Let’s face it—accessing IoT devices securely over SSH on AWS is no walk in the park, but it's definitely a game-changer for modern developers. In this article, we’re going to break down everything you need to know about accessing IoT SSH AWS, from setup to troubleshooting, and everything in between. So, buckle up, grab your favorite coding snack, and let’s dive in!
Now, you might be wondering why we’re even talking about IoT SSH AWS in the first place. Well, here's the deal: as more devices get connected to the internet, managing them remotely becomes essential. Whether you're a small business owner or a full-fledged enterprise architect, secure remote access to IoT devices is crucial. And guess what? AWS has got your back with its powerful tools and services.
Before we jump into the nitty-gritty, let’s set the stage. This article isn’t just another tech tutorial—it’s your go-to guide for mastering secure IoT SSH connections on AWS. We’ll cover everything from configuring SSH keys to optimizing your IoT devices for maximum security. By the end of this read, you’ll be ready to tackle even the most complex challenges in IoT SSH AWS management. So, are you ready? Let’s get started!
Read also:Cloudysocial Greg Minison The Man Revolutionizing Digital Marketing
What Is IoT SSH AWS and Why Should You Care?
In simple terms, IoT SSH AWS refers to the process of securely accessing Internet of Things (IoT) devices using SSH (Secure Shell) over Amazon Web Services (AWS). Think of it as a bridge that connects your local workstation to remote IoT devices hosted on AWS. Why does this matter? Because IoT devices are everywhere—from smart home appliances to industrial sensors—and ensuring their security is paramount.
SSH itself is a cryptographic network protocol that allows secure communication between devices. When combined with AWS, it provides a scalable and reliable solution for managing IoT devices from anywhere in the world. But here’s the catch: without proper configuration, your IoT devices could be vulnerable to cyberattacks. That’s why understanding how to properly set up IoT SSH AWS is so important.
Why Choose AWS for IoT SSH?
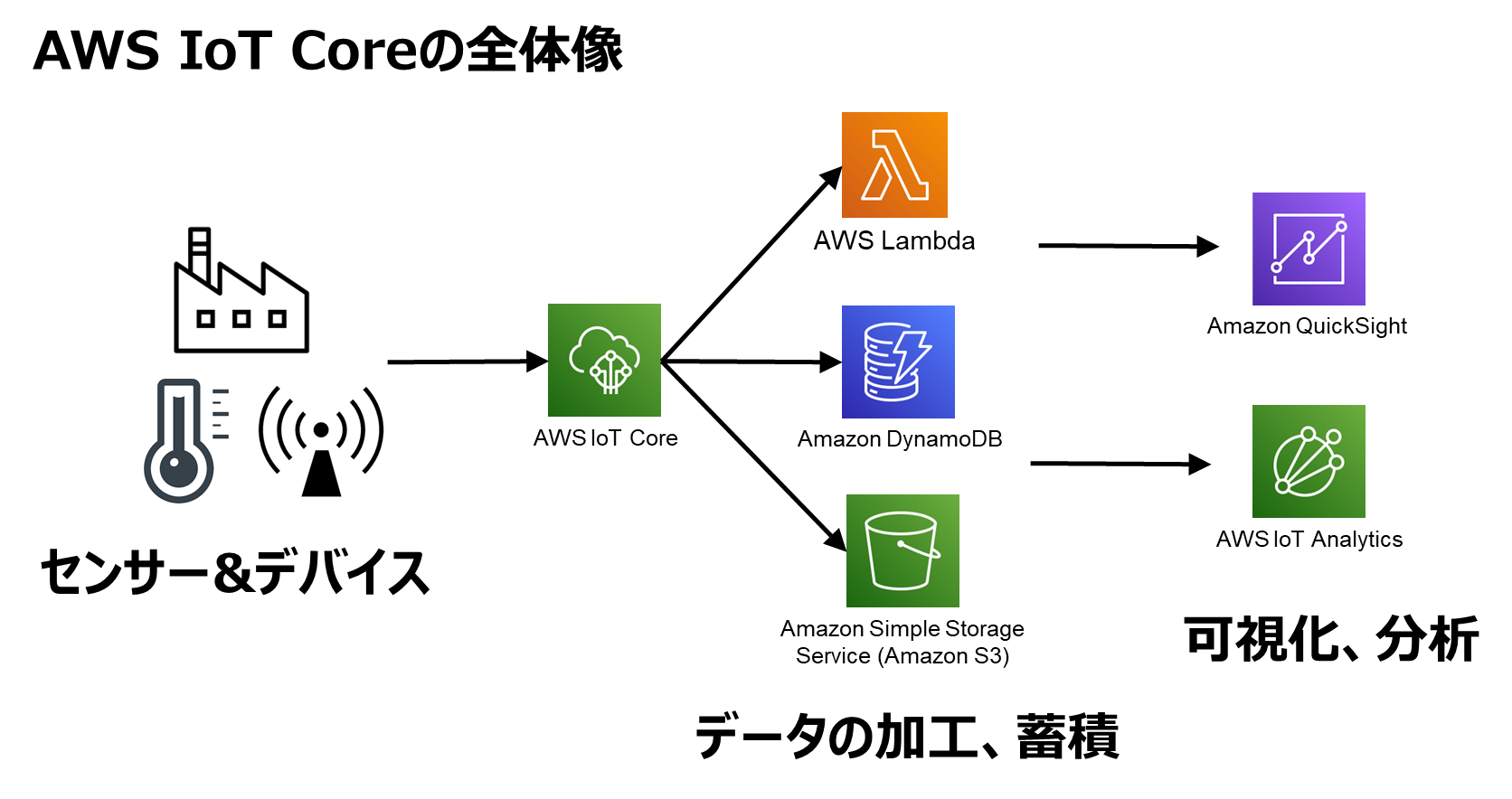
AWS offers a robust ecosystem for IoT development, including services like AWS IoT Core, AWS IoT Device Management, and AWS Systems Manager. These tools make it easier than ever to manage IoT devices at scale. Plus, AWS provides built-in security features like IAM roles, VPCs, and encryption, ensuring your data stays safe.
- AWS IoT Core: A managed cloud service that lets you securely interact with billions of devices.
- AWS IoT Device Management: Helps you organize, monitor, and manage IoT devices throughout their lifecycle.
- AWS Systems Manager: Allows you to remotely manage and troubleshoot IoT devices.
Setting Up IoT SSH AWS: Step-by-Step Guide
Setting up IoT SSH AWS might sound intimidating, but with the right steps, it’s actually pretty straightforward. Below, we’ll walk you through the entire process, from creating an AWS account to establishing a secure SSH connection.
Step 1: Create an AWS Account
First things first—you’ll need an AWS account. If you don’t already have one, head over to the AWS website and sign up. Don’t worry; AWS offers a free tier that’s perfect for beginners.
Step 2: Set Up AWS IoT Core
Once your account is ready, navigate to the AWS Management Console and open the IoT Core dashboard. Here, you’ll create a new thing (AWS lingo for an IoT device) and generate certificates and private keys for secure communication.
Read also:Filmyfly Your Ultimate Destination For Latest Movies And Series
Step 3: Configure SSH Access
Now comes the fun part—configuring SSH access. You’ll need to:
- Create an EC2 instance on AWS.
- Generate and upload SSH keys to your EC2 instance.
- Set up security groups to allow SSH traffic.
Best Practices for Securing IoT SSH AWS
Security should always be at the forefront of your mind when working with IoT SSH AWS. Here are some best practices to keep your devices safe:
- Use strong, unique passwords for SSH access.
- Disable password authentication and rely solely on SSH keys.
- Restrict SSH access to specific IP addresses using security groups.
- Regularly update your IoT devices and software to patch vulnerabilities.
Common Security Threats in IoT SSH AWS
While AWS provides robust security features, it’s still important to be aware of potential threats. Some common risks include:
- Brute-force attacks on SSH passwords.
- Man-in-the-middle attacks intercepting SSH traffic.
- Unsecured IoT devices being exploited by hackers.
Troubleshooting IoT SSH AWS Connections
Even the best-laid plans can go awry. If you’re having trouble connecting to your IoT devices via SSH on AWS, here are a few troubleshooting tips:
- Check your security group settings to ensure SSH traffic is allowed.
- Verify that your SSH keys are correctly configured.
- Ensure your IoT device is properly connected to the internet.
Common Errors and How to Fix Them
Here are some common errors you might encounter and how to resolve them:
- Error: "Connection refused." Fix: Double-check your security group rules.
- Error: "Permission denied (publickey)." Fix: Verify your SSH key pair.
- Error: "Timeout." Fix: Check your network connection and firewall settings.
Optimizing IoT SSH AWS Performance
Once you’ve got your IoT SSH AWS setup running smoothly, it’s time to think about performance. Here are a few tips to optimize your setup:
- Use load balancers to distribute traffic across multiple IoT devices.
- Implement caching mechanisms to reduce latency.
- Monitor your system’s performance using AWS CloudWatch.
Using AWS Lambda for Automation
AWS Lambda is a powerful tool for automating tasks in your IoT SSH AWS setup. For example, you can use Lambda functions to:
- Automatically generate and rotate SSH keys.
- Monitor device health and send alerts when issues arise.
- Perform routine maintenance tasks like backups and updates.
Real-World Use Cases for IoT SSH AWS
So, how are real businesses using IoT SSH AWS? Here are a few examples:
- Smart cities using IoT devices to monitor traffic and manage public infrastructure.
- Manufacturing plants deploying IoT sensors to track equipment performance.
- Healthcare providers using IoT devices to monitor patient vitals remotely.
Case Study: Smart Agriculture
One exciting use case for IoT SSH AWS is in the field of smart agriculture. Farmers are using IoT devices to monitor soil moisture, weather conditions, and crop health. By connecting these devices to AWS and accessing them via SSH, farmers can make data-driven decisions to improve yields and reduce costs.
Future Trends in IoT SSH AWS
As technology continues to evolve, so too does the world of IoT SSH AWS. Here are a few trends to watch out for:
- Increased adoption of edge computing for faster data processing.
- Advancements in AI and machine learning for predictive maintenance.
- Greater emphasis on cybersecurity measures to protect IoT devices.
The Role of 5G in IoT SSH AWS
With the rollout of 5G networks, we’re seeing a new era of connectivity for IoT devices. Faster speeds and lower latency mean more opportunities for innovative IoT applications. AWS is already preparing for this shift by enhancing its IoT services to support 5G-enabled devices.
Conclusion: Mastering IoT SSH AWS
And there you have it—a comprehensive guide to accessing IoT SSH AWS. From setting up your first IoT device to optimizing performance and securing your connections, we’ve covered all the bases. Remember, the key to success in IoT SSH AWS is staying informed and proactive.
So, what’s next? Take action! Whether it’s setting up your own IoT SSH AWS environment or exploring new use cases, the possibilities are endless. And don’t forget to share this article with your fellow tech enthusiasts—knowledge is power, after all.
Table of Contents
- Access IoT SSH AWS: Your Ultimate Guide to Secure Remote Connections
- What Is IoT SSH AWS and Why Should You Care?
- Why Choose AWS for IoT SSH?
- Setting Up IoT SSH AWS: Step-by-Step Guide
- Step 1: Create an AWS Account
- Step 2: Set Up AWS IoT Core
- Step 3: Configure SSH Access
- Best Practices for Securing IoT SSH AWS
- Common Security Threats in IoT SSH AWS
- Troubleshooting IoT SSH AWS Connections
- Common Errors and How to Fix Them
- Optimizing IoT SSH AWS Performance
- Using AWS Lambda for Automation
- Real-World Use Cases for IoT SSH AWS
- Case Study: Smart Agriculture
- Future Trends in IoT SSH AWS
- The Role of 5G in IoT SSH AWS
- Conclusion: Mastering IoT SSH AWS